To take advantage of of conclude-consumer stability computer software, staff have to be educated about how to utilize it. Crucially, keeping it functioning and updating it commonly makes sure that it may safeguard people in opposition to the latest cyber threats.
3rd-social gathering danger assessments are an essential TPRM system, and the ideal hazard evaluation workflows will contain a few phases: research, conducting periodic cybersecurity threat assessments, and refining threat assessment system.
org’s danger repository to ensure the seller’s product or service effectively detects evasions and blocks exploits. Functionality assessments demonstrate if the vendor’s Alternative can get reliable site visitors hundreds without the need of packet reduction and can properly carry out less than distinct ciphers for HTTPS with out higher-effectiveness degradation.
Phishing assaults: Phishing frauds are The most persistent threats to private techniques. This exercise entails sending mass email messages disguised as getting from respectable sources to a list of buyers.
Service suppliers have to verify data security controls and security efficiency to future buyers. While SOC stories and certifications provide prospective buyers and prospects some information regarding corporate protection posture, these level-in-time assessments have limits.
Go with a threat management framework to guidance efficient remediation attempts and waive detected challenges that don't implement to the aims or fears.
SecurityScorecard protection ratings supply transparent facts not merely about likely weaknesses in endpoint safety but also specify which IP addresses are impacted.
Designed for fast implementation and actual organizational use, it really works along with your present tools — so you're able to commit fewer time onboarding and much more time lowering possibility.
Keep away from prospective breaches or compliance problems that might result in pricey penalties or reputational damage.
Making sure your Firm’s third-occasion inventory is exact involves two key measures: examining contractual agreements and economical statements to recognize partnerships which have not been extra towards your inventory possibility and deploying a third-bash threat administration application, like UpGuard CyberSecurity Vendor Risk, to track changes in a 3rd-bash’s protection posture through their lifecycle.
A more in-depth evaluate A few of these third party hazard management worries can drop light-weight on why TPRM courses are Specifically vital right now.
Gartner disclaims all warranties, expressed or implied, with regard to this exploration, together with any warranties of merchantability or Health for a specific reason.
Using stability ratings might help prioritize remediation among present third functions, determine obligatory thresholds for cybersecurity For brand spanking new distributors, assist in earning selections within the procurement course of action, and help outline the extent of evaluation necessary for every seller.
This element lets UpGuard people to know which alternatives and expert services Just about every 3rd-social gathering vendor makes use of and more contextualize their third-party risk assessment procedure.
 Edward Furlong Then & Now!
Edward Furlong Then & Now! Emilio Estevez Then & Now!
Emilio Estevez Then & Now!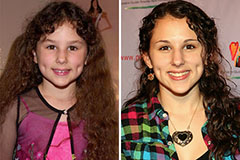 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Heath Ledger Then & Now!
Heath Ledger Then & Now! Sydney Simpson Then & Now!
Sydney Simpson Then & Now!